"Other Network Devices"
WHAT ARE THE OTHER NETWORK DEVICES?
The Bridge
A bridge is a network device that is primarily designed to connect and filter traffic between different segments of a local area network (LAN). Its fundamental purpose is to enhance network performance and efficiency by selectively forwarding data packets based on the hardware (MAC) addresses of devices within the network.
Bridges are deployed to segment larger networks into smaller, more manageable segments, thereby reducing the overall network traffic and improving the overall performance of the system. By examining the destination MAC address of each incoming packet, a bridge intelligently determines whether to forward the data to the destination segment or filter it, preventing unnecessary traffic from reaching segments where it is not required. This selective forwarding helps minimize collisions and congestion, optimizing the flow of data within the network.
Typically located at the boundary between different network segments, bridges play a crucial role in connecting disparate parts of a LAN and facilitating efficient communication between devices. They contribute to the overall stability and reliability of a network by preventing unnecessary broadcast storms and allowing for better organization of network traffic. Overall, bridges serve as integral components in network infrastructure, enhancing performance and ensuring seamless communication between devices within a local network.
Types of Bridges
Transparent bridge
- It derives its name from the fact that the devices on the network are unaware of its existence. A transparent bridge does nothing except block or forward data based on the MAC address.
Source route bridge
- It is used in Token Ring networks. The source route bridge derives its name from the fact that the entire path to be taken by the packet through the network is embedded within the packet.
Translational bridge
- It is used to convert one networking data format to another; for example, from Token Ring to Ethernet, and vice versa.
The Network Card
A network card, also known as a network interface card (NIC) or Ethernet adapter, is a hardware component that enables a computer or other device to connect to a local area network (LAN) or the broader internet. The network card is typically installed inside a computer and serves as the interface between the device and the network, facilitating the transmission and reception of data over the network.
The primary function of a network card is to convert data from the computer into a format that can be transmitted over the network, and vice versa. It achieves this by encapsulating data into packets and utilizing a unique hardware address, known as the Media Access Control (MAC) address, to identify the device on the network. Network cards play a crucial role in establishing and maintaining communication between devices within a network, enabling the exchange of information and the execution of various network-based applications.
Located within a computer, the network card can be an integrated component on the motherboard or a separate expansion card that is inserted into an available expansion slot. The physical connection between the network card and the network is typically established through an Ethernet cable, which plugs into the card's RJ45 port. Wireless network cards, commonly found in laptops and mobile devices, connect to the network through Wi-Fi signals. In essence, the network card serves as the gateway for a device to participate in networked communication, facilitating data transfer and enabling seamless connectivity within the digital infrastructure.
The Modem
A modem, short for modulator-demodulator, is a crucial network device that facilitates the transmission of digital data over analog communication lines. Its primary function is to modulate digital signals from a computer or other digital device into analog signals for transmission over traditional telephone lines and demodulate incoming analog signals back into digital data. Modems are essential for enabling communication between digital devices and the analog infrastructure of the Public Switched Telephone Network (PSTN) or cable systems.
The uses of modems extend across various scenarios, including providing internet access, establishing connections for voice communication, and enabling the transfer of data between devices over long distances. In the context of internet connectivity, a modem acts as the interface between a user's computer and the internet service provider (ISP), allowing the transmission of data over cable, DSL, fiber-optic, or other communication channels. Modems are also employed in scenarios where direct digital communication is not feasible, such as in remote areas with limited infrastructure, utilizing traditional telephone lines for data transfer.
Typically located at the user's premises, a modem can be a standalone device or integrated into other networking equipment, such as a router. In broadband setups, a cable modem or DSL modem connects to the ISP's network, providing users with high-speed internet access. Modems play a pivotal role in bridging the gap between digital devices and analog communication infrastructure, serving as a critical link in various communication systems and enabling the seamless exchange of data in both residential and business environments.
The Transceivers
A transceiver, short for transmitter-receiver, is a versatile network device that combines both functions of transmitting and receiving data within a network. Transceivers serve a crucial role in facilitating communication by converting electrical signals into optical or radio frequency signals for transmission and vice versa. These devices are commonly used in various networking technologies, including Ethernet, wireless communication, and fiber optic networks.
The primary function of a transceiver is to enable bidirectional communication by converting digital data generated by a computer or network device into a form suitable for transmission over the specific medium, such as copper cables, fiber optics, or radio waves. In the receiving mode, the transceiver then demodulates incoming signals, converting them back into digital data for processing by the receiving device. Transceivers are adaptable to different networking environments, providing the flexibility to support various communication protocols and media types.
Transceivers are found in different locations within a network, depending on the technology and application. For instance, in Ethernet networks, a transceiver may be integrated into a network interface card (NIC) or exist as a separate module connected to the device. In wireless networks, transceivers are embedded in devices like routers and access points to facilitate communication over radio frequencies. Fiber optic transceivers, also known as optical transceivers or fiber optic transponders, are used to transmit data over optical fibers and are commonly deployed in networking equipment like switches and routers.
Overall, transceivers play a pivotal role in enabling the seamless exchange of data within networks, providing the necessary interface to adapt to diverse communication mediums and ensuring efficient bidirectional communication across various technologies.
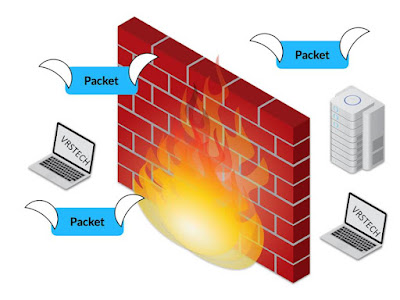
The Firewall
A firewall is a network security device designed to monitor, filter, and control incoming and outgoing network traffic based on predetermined security rules. Its primary function is to establish a barrier between a trusted internal network and untrusted external networks, such as the internet, in order to prevent unauthorized access, protect sensitive data, and mitigate potential cyber threats. Firewalls inspect and manage traffic based on predefined rulesets.
The uses of a firewall extend beyond simple traffic filtering; they include the prevention of unauthorized access attempts, the detection and blocking of malicious content, and the enforcement of network security policies. Firewalls can be configured to permit or deny traffic based on factors like IP addresses, port numbers, and application protocols, providing a crucial defense mechanism against cyber attacks, malware, and other potential security breaches.
Typically located at the perimeter of a network, firewalls serve as the first line of defense against external threats. They can be implemented as hardware appliances, software applications, or a combination of both. In enterprise environments, firewalls are often integrated into network devices such as routers and switches, forming a comprehensive security infrastructure. Additionally, they play a crucial role in securing individual devices within a network by inspecting and filtering traffic at various layers, ensuring that only authorized and safe data is allowed to pass through the network boundary. Overall, firewalls are fundamental components in safeguarding the integrity and security of networked systems.
Image Sources: https://i.ibb.co/2NFS67b/what-is-bridge.png, http://images.esellerpro.com/2131/I/510/3/DCP_3429.JPG, https://www.bhphotovideo.com/images/images1500x1500/netgear_dm200_100nas_broadband_high_speed_dsl_modem_1350766.jpg, https://www.tejar.pk/media/catalog/category/Network-Transceivers_1.png, https://www.vrstech.com/blog/wp-content/uploads/2018/05/network-security-firewall.jpg





.png)

Comments
Post a Comment